

|
Edward Lowton
Editor |


|
| Home> | Efficient Maintenance | >Software | >ICS Protection |
ARTICLE
ICS Protection
11 October 2016
Transporting data to and from devices in the ICS infrastructure increases the risks of malicious code entering your control systems.
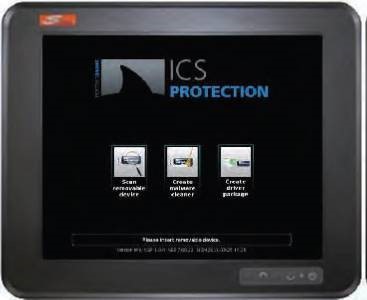
Norman Shark ICS Protection from M.A.C Solutions secures your systems against USB-borne malware threats by enforcing iron-clad security policies across the entire ICS infrastructure.
Computers running Norman Shark ICS Protection Agent will not accept any removable USB media device that has not been scanned and validated by the USB scanner station, thereby blocking all file transfer and application execution from unauthorized devices.
The system can be rapidly deployed in three easy steps: (1) Install the scanner station; (2) Create user agents; and (3) Installing user agents on ICS computers you want to protect.MORE FROM THIS COMPANY
OTHER ARTICLES IN THIS SECTION

















